Industrial IT/OT Zero Trust

Manufacturing network boundaries are becoming fuzzy as external business applications requiring trusted access to plant data perforate the once rigid perimeter. Zero Trust is an approach centered on the concept that a network device should not automatically trust anything inside or outside its perimeters.
https://www.linkedin.com/pulse/industrial-itot-zero-trust-shrinking-your-security-bill-mueller/
Zero Trust is an approach to network and application security gaining momentum in industry. It is centered on the belief that a network device should not automatically trust anything inside or outside its perimeters. Manufacturing network boundaries are becoming fuzzy as external business applications requiring trusted access to plant data perforate the once rigid perimeter.
The plant equipment and network infrastructure we have been putting in for our clients are increasingly designed to co-exist with the existing business infrastructure. The traditional line-in-the-sand firewall or DMZ between these networks remain good practice. But this approach relies on a high-level of expertise to provide and maintain good Access Control Lists.

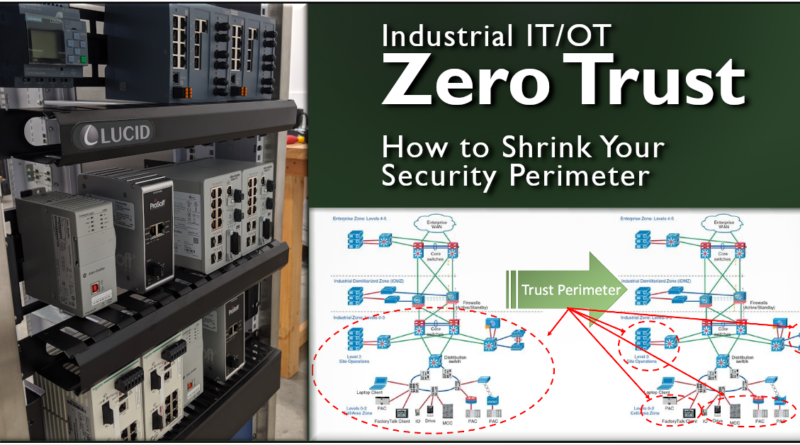
While we may not yet be able to cost-effectively authenticate all ICS traffic, Rockwell and Cisco have produced a security appliance that will allow us to shrink the trusted perimeter to encompass just the end-point process equipment and allow business equipment to share the common infrastructure (such a VOIP phones, security cameras, or access points). The tools that came with the device for deep packet inspection provided a surprising high granularity for access control and intrusion detection.
We got our hands on a din-mount Stratix 5950 unit for bidding an upcoming project. It is similar to the Cisco ISA 3000 device, but with additional features that we’re going to use to integrate into their existing FactoryTalk environment. The initial configuration dashboard will look familiar to those that have used the web-based interface to configure any of the other Stratix devices

Initially, the project requirements were limited to a stateful ASA firewall with NAT that could be easily added to a remote OEM skid panel. Configuring the initial ACL ruleset was straightforward and setup was as expected. Just a simple “deny all incoming except for a specific PI interface read on port X” rule. This effectively created a small trusted perimeter encompassing the local skid-mounted HMI, PLC, and Mass Flow Meter. As an aside, I highly, highly recommend reading the NIST Guideline on Firewall Policy if you haven’t read it yet.
NIST Guideline of Firewall Policy (Special Publication 800-41) https://ws680.nist.gov/publication/get_pdf.cfm?pub_id=901083
Since we had it, we also tried enabling the basic FirePOWER traffic analysis module to get a better handle on what exactly the device provided for threat detection and intrusion prevention. It was straightforward to setup from the web utility. The additional monitoring was useful, but I’m sure we are just scratching the surface of the device’s capabilities. Here is what we found in the short time we messed with it based on the ODVA CIP class operations:

We enabled the Deep Packet Inspection preprocessor for common CIP traffic. Our setup was a simple FT View SE project (VM), compact logix, and laptop running RSLogix. From the device, we could set policies to individually allow CIP reads, CIP writes, and CIP Admin functions.
The way the device processes incoming traffic is that it is first run through the ASA Firewall policy. If traffic is not allowed, packets are dropped to the ether without further processing. If allowed and you’ve enabled the DPI functions, packets are then forwarded to the preprocessor to determine if it complies with the access policy. If good, the packets are forwarded to their destination.

The interesting part is when unauthorized access is detected. The recommended action is to “Block and Reset” the connection. The packet is dumped to /dev/null, but the appliance actively spoofs the destination device and sends a TCP reset the originating device. Blocked traffic also appeared on the dashboard screen and there was an option to configure it as an alarm.
Approaching Zero Trust from the application level, the Stratix 5950 allows policies to be integrated with FactoryTalk Security and tied to an individual user/group. These controls seemed similar to existing controls available from the FT Administration console, but it allowed a further refined level of security on a per-application basis.
A ruggedized industrial firewall capable of being mounted directly into a control panel helped us meet our project requirements. With the addition of the DPI access control functions, a solid use case can be made for a remote plant zone panel that aggregates a set of field device connections to a shared stack of IT-managed distribution switches. Process equipment will operate a little more securely in a smaller trust perimeter when sharing plant and business network infrastructure.
While we still have a ways to go for a full Zero Trust implementation, shrinking the perimeter of trusted traffic closer to the endpoint equipment it is a solid step towards a layered security approach in mixed-use network infrastructure environments.
Contact us to see how we may help secure your process equipment at info@lucidautomationsecurity.com

Note: Article originally published in August, 2019. The content is applicable in today’s environment and a second post with refreshed graphics may help those designing these systems.